The hacking group ShinyHunters has allegedly leaked millions of records from SoundCloud and Crunchbase following unsuccessful extortion attempts, potentially indicating a connection to an Okta vishing campaign.
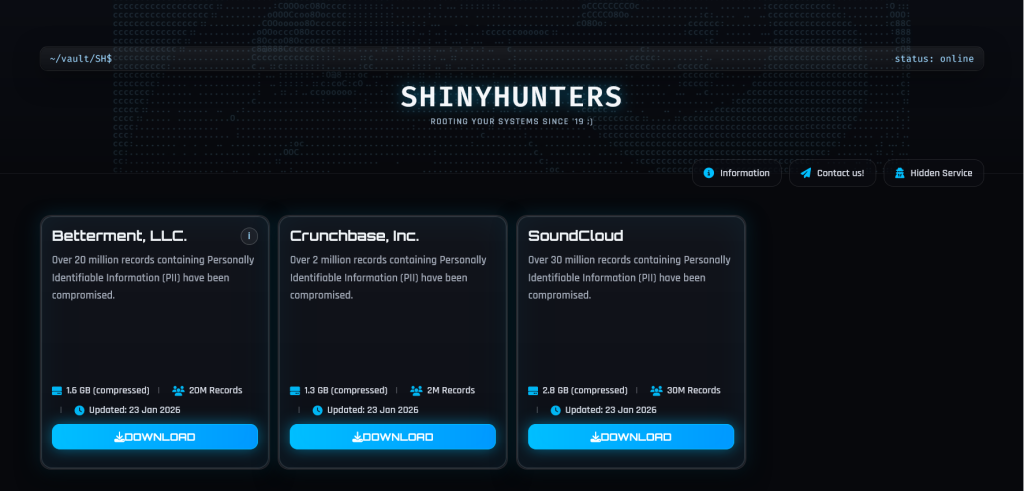
ShinyHunters, a notorious cybercriminal collective, has resurfaced in the cybersecurity news landscape. The group has launched a leak site on the dark web, where they claim to have released partial databases from three notable companies: SoundCloud, a leading global audio streaming service; Crunchbase, a platform that catalogs company data; and Betterment, an American financial advisory firm.
The leaks became public on January 22, 2026, as messages surfaced on the group’s Telegram channel, directing users to .onion domains that purportedly contain the stolen data. The group stated that the data was released due to failed ransom negotiations with the affected companies, a tactic increasingly seen among cybercriminal organizations.
In a bold message posted on their leak site, ShinyHunters stated, “We are after corporate regime change in all parts of the world. Pay or leak. We will aggressively and viciously come after you once we have your data. By the time you are listed here, it will be too late.” This approach underscores a clear intent to instill fear in corporate targets, aligning with tactics often categorized under MITRE’s ATT&CK framework, such as coercion and exploitation of sensitive data.
In December 2025, SoundCloud acknowledged a data breach affecting about 20% of its user base. Given SoundCloud’s reported 175 to 180 million users, the estimated 35 to 36 million compromised accounts aligns closely with the quantities mentioned in ShinyHunters’ disclosures. The group’s recent claims suggest a potentially significant impact on the affected companies and their users.
Potential Okta Connection
Concurrent with the leaks, Okta, a cloud-based Identity and Access Management provider, issued a security advisory regarding an ongoing vishing campaign targeting their single sign-on functionality. Reports indicate that the campaign has already led to multiple incidents, although the full extent remains unclear.
Alon Gal from Hudson Rock, a cybersecurity firm, reported via LinkedIn that ShinyHunters have acknowledged their involvement in the Okta vishing campaign and suggested that further data leaks are imminent. This statement raises significant questions about the interconnectedness of these incidents and the methodologies employed by the attackers.
While the specific links between the three alleged breaches and Okta require further investigation, Hackread.com has reached out directly to ShinyHunters for clarification. Currently, evidence suggests that the data related to all three companies is circulating widely on cybercrime forums, particularly within French and Russian language communities.
As Hackread.com continues to engage with SoundCloud, Crunchbase, and Betterment for official comments, it is imperative to note that until these organizations verify the authenticity of the leaked data, the claims surrounding these breaches should be approached with caution and skepticism.