
In a troubling development, the ShinyHunters extortion group has claimed responsibility for a series of voice phishing attacks, specifically targeting single sign-on (SSO) accounts associated with major platforms such as Okta, Microsoft, and Google. These attacks allow cybercriminals to infiltrate corporate Software as a Service (SaaS) platforms and exfiltrate sensitive company data, which is then utilized for extortion.
The modus operandi of the attackers involves impersonating IT support personnel. They contact employees directly, deceiving them into providing their login credentials as well as multi-factor authentication (MFA) codes through phishing sites that mimic legitimate company login pages. This technique effectively undermines the security mechanisms typically employed by these organizations.
Upon successfully compromising an SSO account, the attackers gain access not only to the initial application but potentially to all connected enterprise services. These interconnected systems can include widely used platforms like Salesforce, Microsoft 365, Google Workspace, Dropbox, and others, making a compromised account a significant threat to overall corporate security.
Single sign-on (SSO) services provided by companies like Okta, Microsoft Entra, and Google streamline authentication across multiple applications, allowing employees to access various cloud services with just one set of credentials. The dashboards of these SSO platforms often display a full list of connected services, turning a breached account into a vulnerability that can lead to extensive unauthorized access.
As reported by BleepingComputer, these vishing (voice phishing) attacks exploit social engineering tactics, whereby attackers persuade employees to log into fraudulent pages while on a phone call. Once they gain control over an SSO account, they can sift through linked applications and harvest sensitive data.
Multiple organizations targeted by these attacks have since received extortion demands from ShinyHunters, illustrating the group’s involvement in the recent breaches. BleepingComputer reached out to Okta, yet the company refrained from commenting on the reported data thefts. However, a recent Okta report outlined the phishing kits utilized in these voice-activated assaults, confirming details consistent with BleepingComputer’s findings.
According to Okta, these phishing kits feature a web-based control interface that allows attackers to modify what the victim views in real time on the phishing site while conversing with them. This capability enables attackers to guide victims step-by-step through the login process and MFA challenges. If attackers input stolen credentials into legitimate services and encounter MFA prompts, they can instantaneously adjust the phishing site to instruct victims on how to approve notifications or enter TOTP codes.
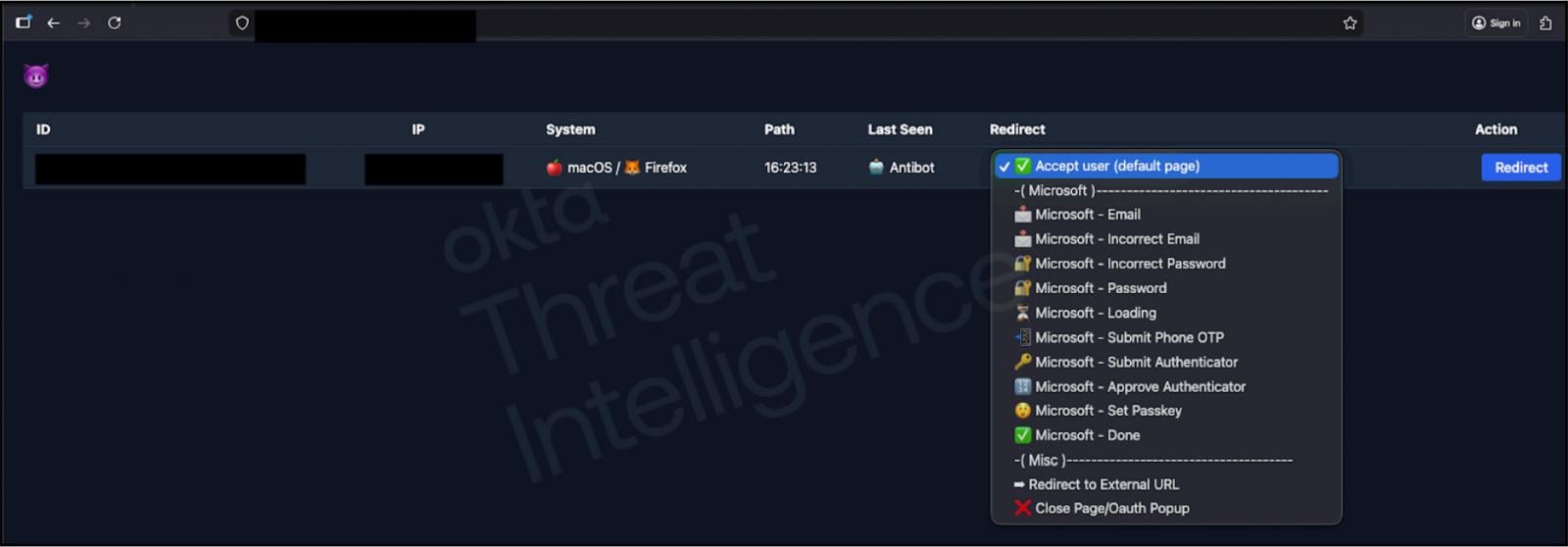
Source: Okta
ShinyHunters confirmed its involvement in these attacks, explicitly stating that they are particularly focused on targeting Salesforce while also leveraging access gained from attacks on platforms like Okta and Microsoft Entra. Although Microsoft and Google have stated they have no evidence their services are being targeted, it remains crucial for businesses to reassess their cybersecurity postures in light of these incidents.
The group reportedly utilizes previously stolen data, including contact details, job titles, and names from past breaches to enhance the credibility of their social engineering tactics. Recently, they have relaunched their Tor data leak site, revealing breaches at firms such as SoundCloud, Betterment, and Crunchbase, raising concerns about the persistent threat posed by cyber extortion groups.
Representatives from Crunchbase confirmed a cybersecurity incident involving the exfiltration of sensitive documents from their corporate network, emphasizing ongoing investigative measures and cooperation with law enforcement. Such breaches necessitate a comprehensive evaluation of security measures and incident response strategies for all organizations involved.

