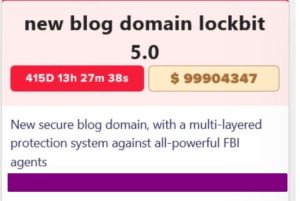
 In a bold announcement reminiscent of previous disclosures, the LockBit 5.0 cybercriminal group recently introduced a new secure blogging domain, claiming it offers a multilayered protective system against law enforcement activities. This declaration, steeped in confidence, comes at a time when scrutiny over their operations has intensified.
In a bold announcement reminiscent of previous disclosures, the LockBit 5.0 cybercriminal group recently introduced a new secure blogging domain, claiming it offers a multilayered protective system against law enforcement activities. This declaration, steeped in confidence, comes at a time when scrutiny over their operations has intensified.
Just days prior, cybersecurity researcher Rakesh Krishnan uncovered crucial information regarding LockBit 5, disclosing the group’s IP address and domain. In a tweet on December 5, Krishnan revealed significant details regarding LockBit 5’s server, explicitly naming the IP address as 205.185.116.233 and the domain as karma0[.]xyz, which is set to remain registered until November 2, 2025.
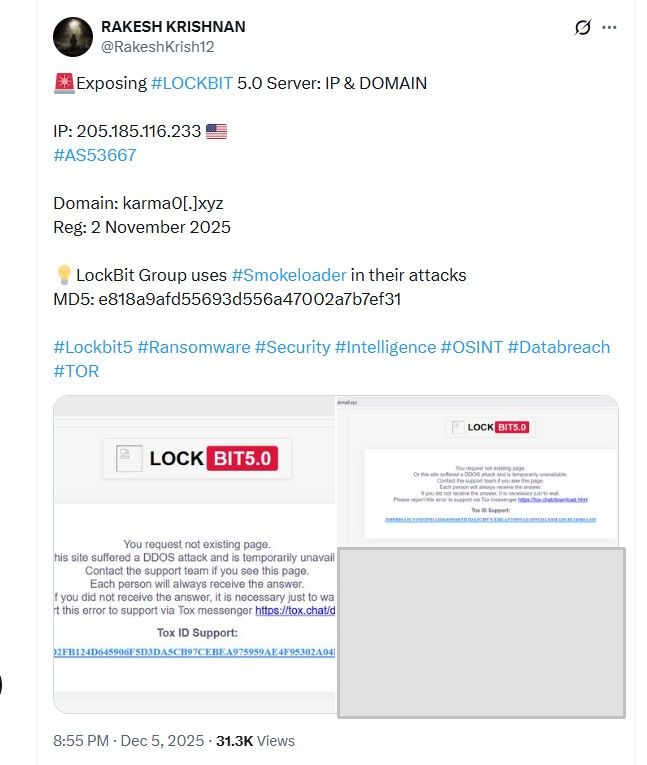
Throughout his post, Krishnan emphasized that the LockBit Group employs the #Smokeloader malware in their attacks, a technique recognized within the MITRE ATT&CK framework, particularly under the initial access and persistence tactics. This incident underscores the continuous evolution of threat actors leveraging malware for unauthorized access, compromising both individual and organizational data integrity.
Furthermore, DataBreaches.net has reported that LockBit 5.0 may have been repurposing dated data, having recently announced 23 new victims on their dark web leak site, with 11 of these targets having previously been disclosed in earlier leaks from April 2025. This recycling of victims raises questions about the group’s operational capacity and the effectiveness of their attacks, suggesting a potential reliance on past data rather than innovative techniques.
In addition, Krishnan noted that two of the victims belong to distinct groups, specifically #Weyhro and #RansomHouse, indicating a broader strategy of targeting multiple sectors, which calls for vigilance among businesses across various industries.
Analysis from Cyber Security News further supports claims of lax operational security (opsec) within the LockBit group. Their scans revealed multiple open ports on the identified IP address, particularly vulnerable remote access points, leaving the server susceptible to disruptions and potentially compelling defenders to take immediate action, such as blocking the IP address and domain.
The ongoing exposure of these vulnerabilities emphasizes critical weaknesses in the group’s operational methods, challenging their claimed security posture. As organizations remain vigilant in monitoring potential breaches, the information shared by researchers like Krishnan is invaluable in identifying emerging threats and fortifying defenses against evolving attack methods.