This week has unfolded with considerable turmoil, particularly for Instagram users, following Malwarebytes’ announcement on January 9 regarding a significant data breach associated with the Meta-owned platform. The cybersecurity firm reported that hackers have leaked information from approximately 17.5 million Instagram accounts online, revealing sensitive details such as usernames, email addresses, phone numbers, and physical addresses.
In a statement on X (formerly Twitter), Malwarebytes described how, according to their findings, cybercriminals compromised the sensitive data of 17.5 million Instagram accounts, providing access to usernames, addresses, phone numbers, emails, and other details.
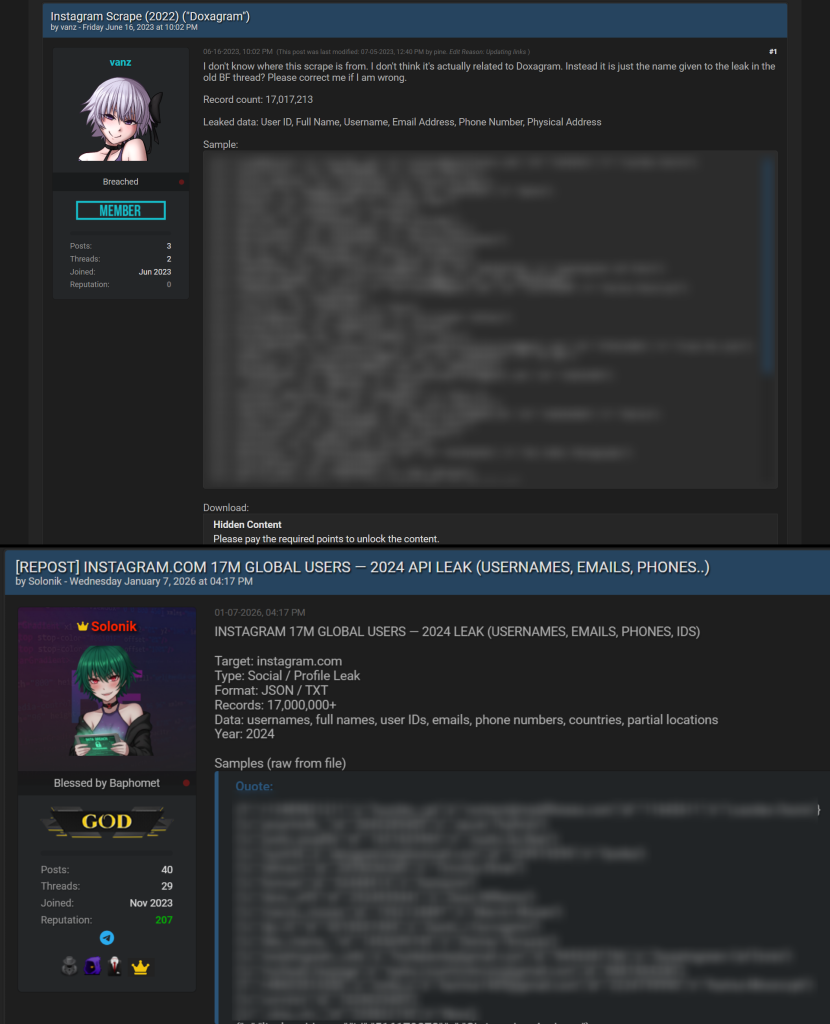
However, further investigation by Hackread.com revealed that the claim of a new breach was misleading. While the data is legitimate, it was not freshly stolen. Malwarebytes cited a BreachForums post from January 7, 2026, authored by a user identified as Solonik, titled “INSTAGRAM.COM 17M GLOBAL USERS – 2024 API LEAK.” This post inaccurately suggested a breach in 2024, though it turned out to be a rehash of data originally compiled in 2022.
Moreover, the data attributed to the supposed 2024 incident echoes an earlier leak first made public on BreachForums in June 2023 by a user named “vanz.” This older dataset also appeared on another forum, LeakBase. The labeling of the data as a fresh breach appears to be a calculated move to revive old information under the guise of new, thereby enhancing perceived credibility.
Analyzing the Numbers
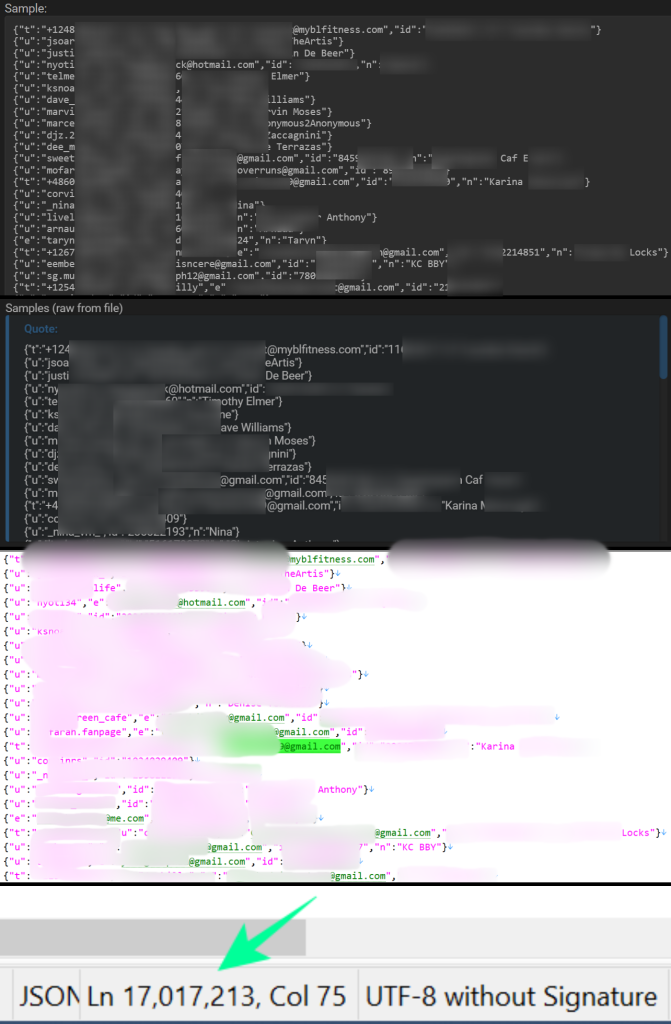
This alleged “latest” Instagram leak comprises exactly 17,017,213 user records, a figure that aligns perfectly with data released by both “vanz” in June 2023 and by “Solonik” in January 2026. A swift examination of the sample datasets confirms they are identical in format and entries. Hackread.com’s review corroborated that the current leak is merely a reiteration of the previously circulated information from 2022.
Password Reset Emails Spark Concerns
Amid rising anxiety about the leak, many users reported receiving unsolicited password reset emails from Instagram. Initial reactions included suspicions of phishing attempts, especially since the leaked dataset did not contain passwords. These emails, sent from Instagram’s verified domain and featuring blue checkmarks, fueled speculation that hackers might have indeed compromised user accounts.
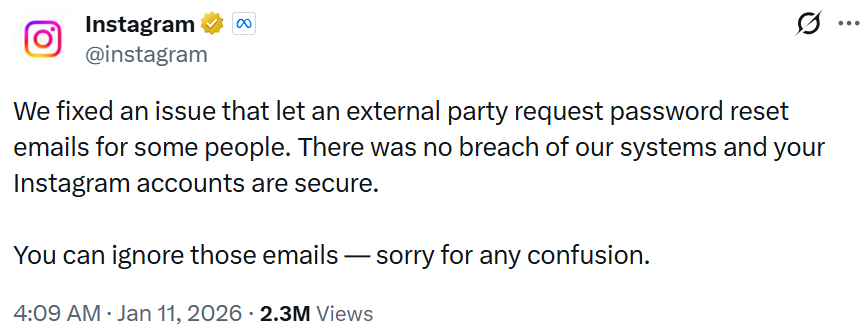
On January 11, 2025, Instagram responded to the uproar on X, categorically denying any breach while clarifying that a glitch had enabled an external party to request password reset emails for selected accounts. “We addressed an issue that allowed an external party to initiate password reset requests for some users. There was no compromise of our systems, and your Instagram accounts remain secure. You can disregard those emails. We apologize for any misunderstanding,” the company tweeted.
This situation raises an important question: Who was the external party that accessed the password reset function, and how were they able to send legitimate emails? It remains ambiguous whether an automated system or an individual exploited Instagram’s password reset feature using usernames from the exposed dataset.
Addressing Sensationalism in Cybersecurity Reporting
A concerning trend in cybersecurity journalism is the emergence of sources acting like tabloids rather than reliable news outlets. These publications frequently rush to publish stories that prioritize sensationalism over accuracy, often relying on unverified claims sourced from social media or Telegram channels without conducting proper fact-checking.
The current Instagram incident exemplifies this issue, showcasing a lack of diligence in confirming the data’s authenticity, age, or context before publishing alarmist headlines regarding breaches. This recklessness inevitably breeds confusion among readers, disrupts accurate security research, and distorts public comprehension of genuine cybersecurity threats.
Advisories for Instagram Users Regarding Scam Risks
Despite the fact that the leaked data is dated, the information within it remains viable for malicious actors to execute targeted phishing and smishing campaigns. Instagram users associated with the dataset should remain vigilant against suspicious emails impersonating Instagram, Meta, or other trusted entities.
These communications might attempt to deceive users into divulging their passwords, clicking on fraudulent links, or downloading harmful attachments. The same scrutiny applies to SMS messages that proclaim urgent security warnings. If you receive any password reset notifications that you did not request, avoid engaging with them. Instead, navigate directly to the app or website to verify any issues. Even recycled data can be exploited, resulting in potential damage long after its initial exposure.