In a significant revelation that raises alarms for professionals regarding online privacy, cybersecurity researcher Bob Diachenko, in collaboration with nexos.ai, uncovered an unsecured MongoDB database on November 23, 2025. This massive dataset, consisting of approximately 16 terabytes (TB) of information, was left exposed on the internet, revealing an astonishing 4.3 billion professional records, which could be exploited by criminals for targeted attacks.
For context, MongoDB is widely adopted by businesses for data storage due to its flexibility and scalability. Diachenko reported that the database was secured just two days after notifying its owner, creating a significant window during which unauthorized access could have occurred.
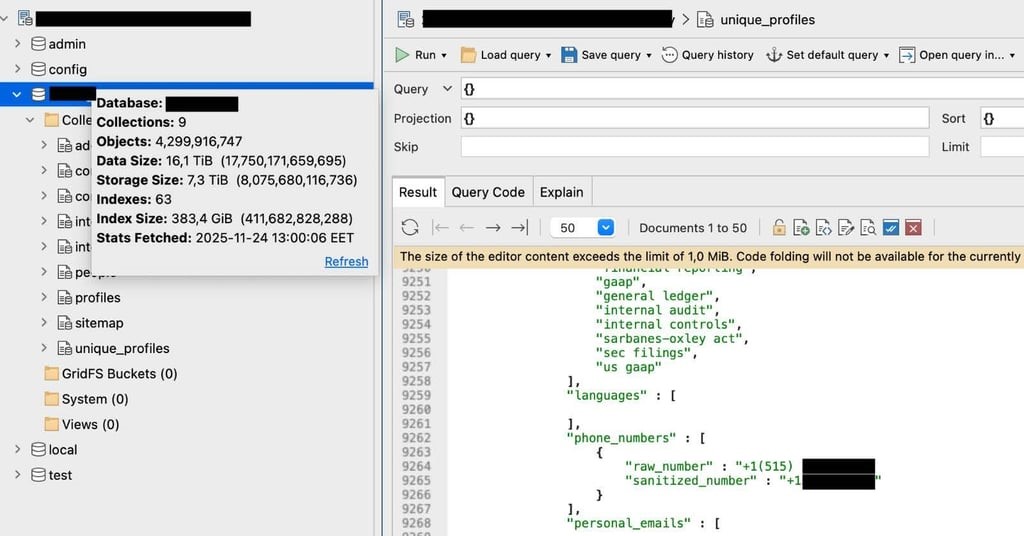
The Discovery and Data Details
A further analysis by the Cybernews team identified that the dataset was partitioned into nine distinct collections, labeled with names such as “profiles,” “people,” and “unique_profiles.” Notably, at least three of these collections laid bare nearly 2 billion personal records. The compromised data included Personally Identifiable Information (PII) encompassing full names, email addresses, phone numbers, job titles, employment history, educational background, and links to professional networking platforms like LinkedIn.
The “unique_profiles” collection alone contained over 732 million records along with images. Additionally, researchers noted that the “people” collection included metrics and identifiers linked to the Apollo.io network. It was pointed out that while records in a specific collection are unique, there may be duplicates across different collections, complicating the scope of data exposure.
The dataset’s structure and volume strongly suggest that the information was aggregated through various means, potentially including web scraping, a common method for gathering data from public sources. The origins of some records may trace back to earlier leaks dating back to 2021.
Who Owns the Data and Why It’s Dangerous
While the identity of the database owner has not been definitively established, investigative efforts indicate a connection to a lead-generation firm that specializes in linking businesses with potential clients. This speculation aligns with the extensive number of records uncovered in the leak. Nevertheless, Cybernews researchers caution against attributing ownership without more evidence, noting that the database could have been scraped rather than originally belonging to the firm.
The implications of such a large-scale data breach are profound. Cybercriminals often seek structured datasets for nefarious purposes, allowing them to conduct highly targeted attacks, such as phishing schemes or CEO impersonation fraud, which can be significantly more challenging for victims to detect. These records could serve as a foundation for cybercriminals to establish comprehensive, searchable databases that simplify attacks on high-value targets, including employees from major corporations.
To mitigate risks, professionals are urged to adopt stringent security measures, including using strong, unique passwords and enabling two-factor authentication (2FA) as well as ensuring software is regularly updated to address vulnerabilities. This breach underscores the importance of maintaining robust cybersecurity practices in today’s digital landscape.
Below is a detailed breakdown of the document counts across the nine collections:
people – 169,061,357 documents (3.95 TB)
profiles – 1,135,462,992 documents (5.85 TB)
sitemap – 163,765,524 documents (20.22 GB)
intent – 2,054,410,607 documents (604.76 GB)
companies – 17,302,088 documents (72.9 GB)
intent_archive – 2,073,723 documents (620 MB)
address_cache – 8,126,667 documents (26.78 GB)
unique_profiles – 732,412,172 documents (5.63 TB)
company_sitemap – 17,301,617 documents (3.76 GB)