A staggering 149 million stolen usernames and passwords for platforms like TikTok, Disney+, Netflix, Roblox, and numerous crypto wallets have been discovered online without any form of security authentication. This incident highlights the critical need to secure your digital identity in light of a recent massive data leak.
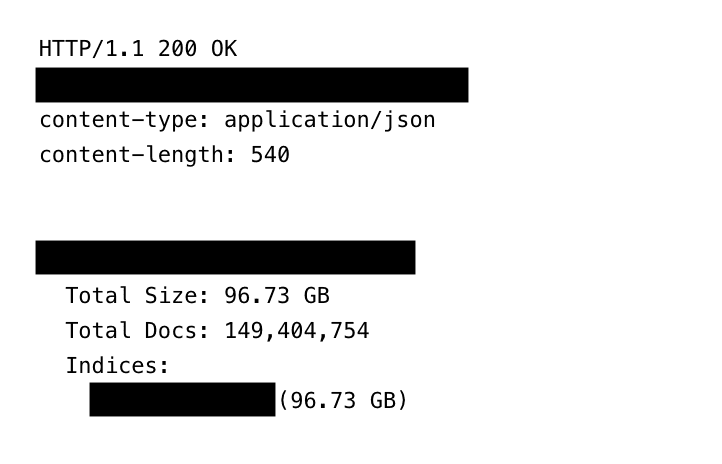
A substantial database holding over 149 million compromised usernames and passwords has recently been taken offline after existing unprotected on the internet for weeks. Noted cybersecurity researcher Jeremiah Fowler identified the exposed information, emphasizing that this exposure underscores the global threat posed by data theft, effectively allowing anyone with internet access to view and search the records. This research was published through ExpressVPN and shared on Hackread.com.
A One-Stop Shop for Hackers
The database, which totaled 96 GB, was not merely a collection of outdated leaks. Fowler noted that during his nearly month-long effort to alert the hosting provider, he observed that the collection was expanding in real time. The scope of the stolen data raises significant concerns. The database comprises accounts spanning various categories, including:
Among the records are approximately 17 million Facebook logins, alongside accounts from Instagram, TikTok, and X. The streaming and gaming sector saw over 3.4 million Netflix logins, in addition to accounts from HBOmax, Disney+, and Roblox. Financially sensitive details were also within this trove, including banking and credit card credentials, as well as 420,000 Binance crypto logins. Furthermore, the data exposed accounts from dating applications and OnlyFans, impacting both creators and their clients.
Concerningly, the database also contained 48 million Gmail accounts, nearly 4 million Yahoo logins, 1.5 million Microsoft Outlook credentials, and approximately 900,000 Apple iCloud login details. Of particular alarm was the inclusion of login information associated with governmental (.gov) domains from various nations, with Fowler observing that even limited access could enable hackers to impersonate officials or penetrate secure governmental networks.
The Mystery of the Infostealer
The source of this extensive dataset is likely linked to infostealer malware, software designed to infiltrate computers or mobile devices to capture inputted information. Fowler’s research indicates that this operation appeared unusually organized compared to past data leaks. Notably, the system employed a methodical labeling approach to categorize data by device type and originating website. This efficiency likely aided criminals in pinpointing victims while evading standard security measures. Each entry featured a unique fingerprint (or hash), ensuring that no duplicates were maintained.
A Month of Exposure
Immediate action is crucial during data breaches, but Fowler encountered numerous challenges in the reporting process. It took a month of repeated attempts before the hosting provider ultimately suspended the server. Unfortunately, the exposure may have already had significant repercussions. Since the records contained precise web URLs, criminals had a simpler path to automate their attacks.
To mitigate risks, utilizing a password manager and activating two-factor authentication is strongly advised. Regularly updating operating systems is another essential practice to address vulnerabilities that malware exploits.