On January 9, 2026, a significant data breach was disclosed involving BreachForums, a well-known hacker forum that operates on both the clear and dark web. The breach has exposed the personal information of over 320,000 users, drawing considerable attention within cybersecurity circles.
BreachForums has a tumultuous history, having been previously seized by law enforcement and often disappearing from the internet only to reemerge later. Following the shutdown of its predecessor, RaidForums in 2022, it quickly became the primary platform for various cybercriminal activities. Yet, in April 2025, the forum briefly vanished, leading to speculation that law enforcement action was responsible.
While many feared a police raid, reports from Hackread.com indicated that the disappearance was due to a security vulnerability instead. By July 2025, BreachForums had successfully returned online.
The Leaked Database
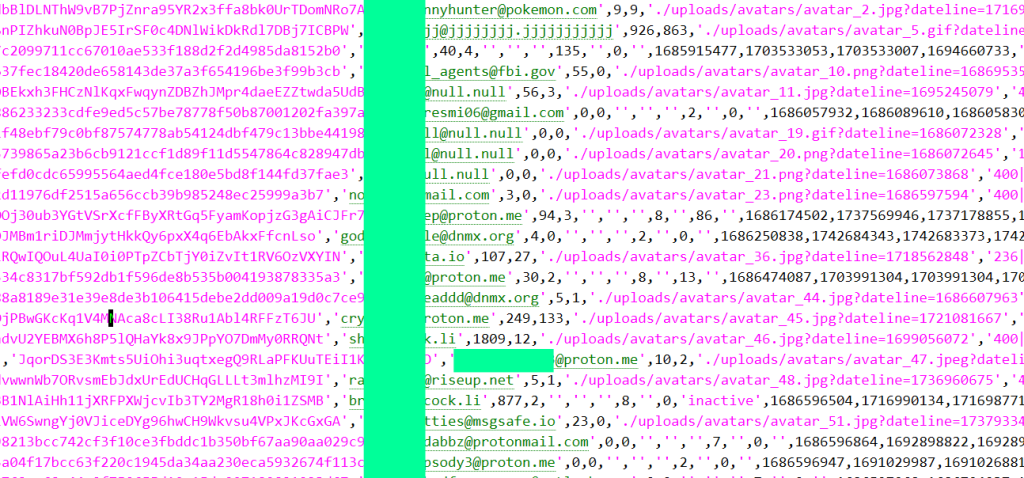
Research from Resecurity, shared with Hackread.com, revealed that the leaked data comprises details of 323,986 users, including metadata sourced from a MySQL database. This metadata presents a digital footprint that could enable identification of users.
The leak surfaced on shinyhunte.rs, a platform known for hosting stolen data, which raises concerns about malicious content. This site has previously been linked to data breaches involving trusted companies such as Fujifilm and Qantas Airways, notably following incidents linked to Salesforce-related compromises.
Accompanying the breach was a valid PGP signature traditionally associated with past operators of the forum, reinforcing the authenticity and demonstrating that the dataset likely originated from internal BreachForums systems.
ShinyHunters, the group associated with this leak, operates as a changing collective of hackers, including factions like Scattered Lapsus$ Hunters. These names signify a coalition of young hackers collaborating to share tools and target valuable data.
According to an independent review conducted by Hackread.com, the leaked dataset not only includes standard profile metadata but also user display names, email addresses, Argon2i password hashes, and links to external accounts like Telegram. Despite the passwords not being in plaintext, the combination of this information poses risks regarding user privacy and identification.
Response from BreachForums
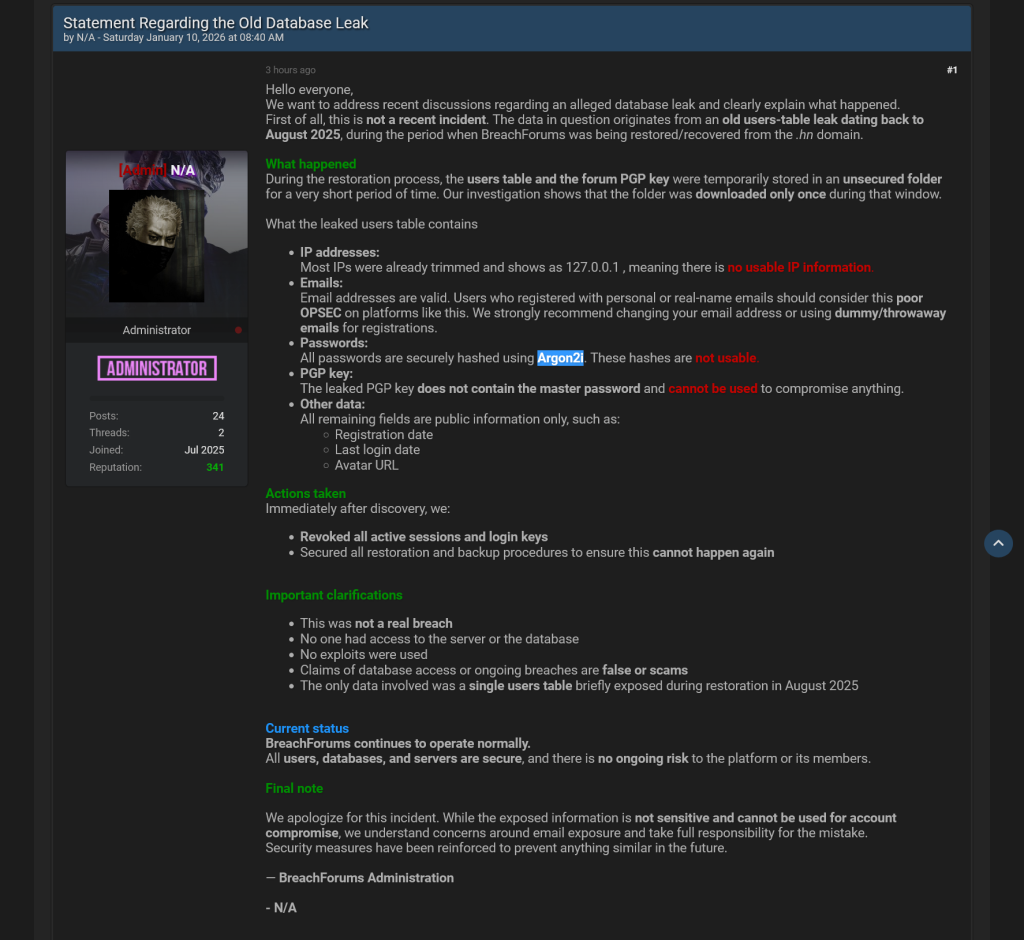
In response to the breach, an administrator from BreachForums, using the alias N/A, asserted that the leaked data stemmed from an earlier incident in August 2025, linked to a restoration procedure following the takedown of their .hn domain. The administrator clarified that the users’ table and the forum’s PGP key had been briefly stored in an unsecured folder, where it was downloaded once.
This official emphasized that the data did not result from a server compromise or database access, labeling claims of an active breach as misleading. Additionally, they noted that passwords were stored with Argon2i hashes, while IP addresses were primarily truncated, and the rest of the fields included only publicly available information. They stated that all user sessions were terminated at the time of the incident, and subsequent restoration methods have been enhanced for security.
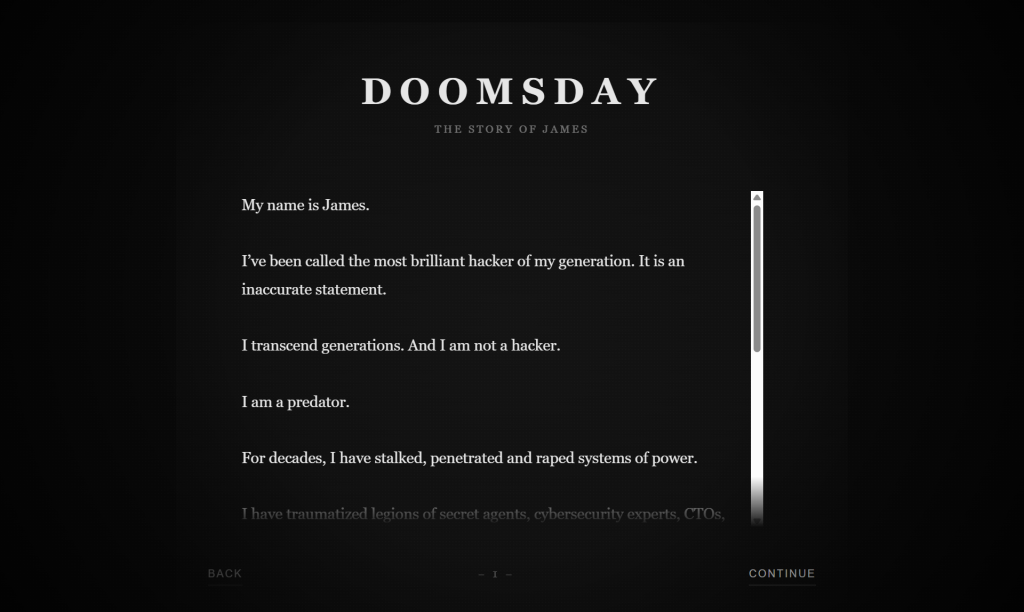
The “James” Message Circulating With the Leak
A manifesto attributed to an individual named “James” accompanied the leaked data on shinyhunte.rs. The text contains extravagant claims, threats, and references to various cybercrime figures, presented in a theatrical and ideological format.
The authenticity of the assertions made within this message has not been independently verified; such manifestos often serve as tools for drawing attention, disseminating misinformation, or muddling attribution within underground forums. The text should be regarded as unverified rhetoric rather than factual information.
Why This Leak Matters
This unprecedented exposure of a criminal organization’s inner workings provides critical insight into the vulnerabilities that even malicious groups face. Analysts believe that revealing such criminal infrastructures can disrupt illicit networks, potentially deterring future recruits. Through independent analysis of the leaked database, researchers aim to dismantle the cycle of cybercrime and encourage individuals to distance themselves from these illegal networks.