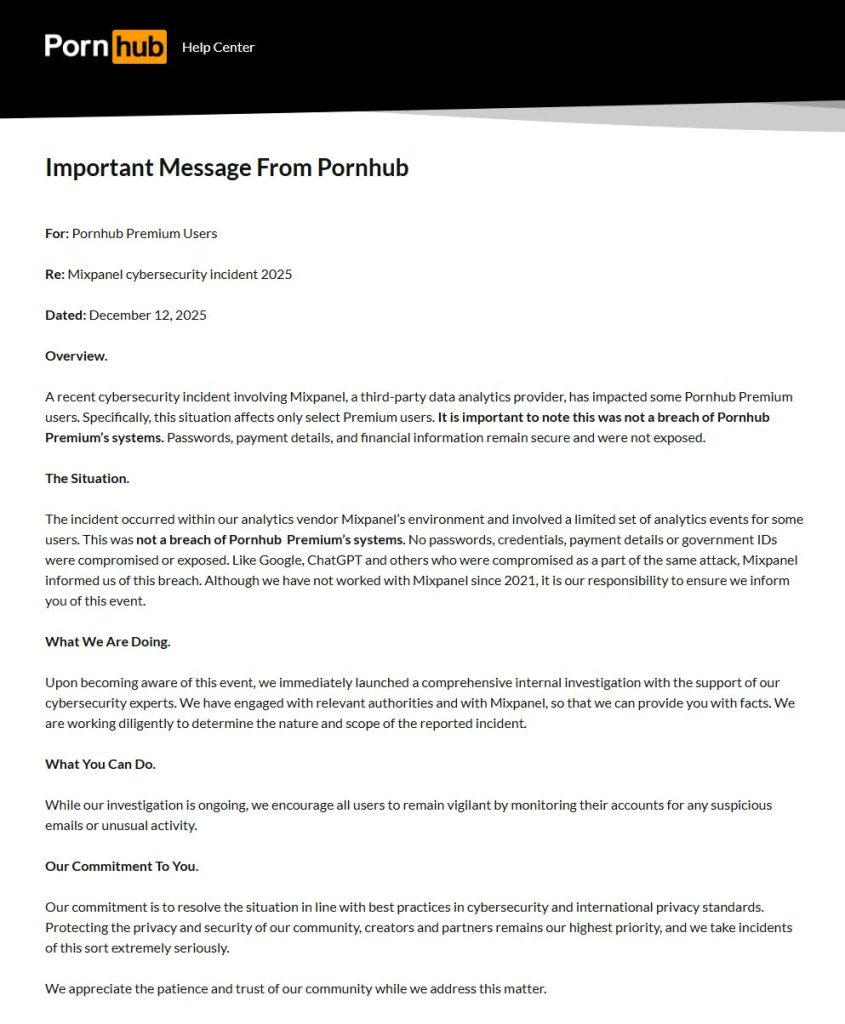
A significant data breach has come to light, involving the personal viewing histories of numerous individuals who previously held accounts with Pornhub Premium. The cybercriminal group ShinyHunters claims responsibility, alleging they have pilfered a 94GB database comprising over 200 million records (specifically 201,211,943) detailing user searches, downloads, and video activities. Following the breach, the group has initiated an extortion campaign, demanding ransom payments in Bitcoin.
According to cybersecurity experts at Rescana, the breach can be traced back to a security lapse at Mixpanel, a third-party analytics provider. Notably, this is the same company that experienced a breach last month, which compromised API user data for OpenAI . Rescana’s analysis indicates that the incident began on November 8, 2025, when hackers executed a smishing attack—sending fraudulent text messages to employees in order to acquire their login credentials—granting unauthorized access to Mixpanel’s systems.
Sensitive Data and Extortion
The compromised data includes sensitive records that contain private information. BleepingComputer has reported that the stolen data encompasses:
Email addresses along with approximate geographical locations (city and country), metadata related to activity such as video titles and URLs, and timestamps indicating when each video was viewed or downloaded.
ShinyHunters has begun sending extortion emails to impacted companies, threatening to release the entirety of the stolen data unless a ransom is paid. However, it is important to note that Pornhub’s internal systems have not been directly compromised. The platform has confirmed that sensitive information such as passwords and credit card details remain secure.
Verifying the Stolen Data
In an effort to validate their claims, ShinyHunters shared data linked to 14 Pornhub Premium users. A report from Reuters confirmed the authenticity of the data after matching details for six individuals against previous records held by District 4 Labs. Notably, three of these individuals acknowledged that they were indeed former subscribers. Although the hackers have not disclosed their precise methods for obtaining the files, this verification indicates that real user information has been exposed.
Conflicting Reports on Data Access
It is also crucial to highlight that, according to Pornhub’s official statement, the platform ceased its use of Mixpanel in 2021, which implies that the exposed records date back at least four years. The narrative becomes convoluted, however, as both entities have since expressed differing perspectives on the breach’s origins.
Initially, Pornhub attributed the breach to Mixpanel, but as of December 16, 2025, those mentions have been omitted from their advisory. Conversely, Mixpanel now claims that the data was last accessed in 2023 via a legitimate account linked to Pornhub’s parent company, Aylo. This suggests that the compromise may stem from a separate account breach rather than an infiltration of Mixpanel’s servers.