
Nokia has confirmed that a recent investigation into allegations of a data breach linked to its operations revealed that the leaked source code, which surfaced on a hacker forum, originates from a third-party vendor. Importantly, the company asserts that neither its internal systems nor customer data has been compromised in this incident.
This development follows claims made earlier this week by an online threat actor known as IntelBroker, who asserted they had accessed sensitive data from Nokia by breaching a third-party vendor’s server. IntelBroker even attempted to monetize this data, which they claimed included SSH keys, source code, RSA keys, and other credentials, before opting to leak the information after Nokia denied the breach.
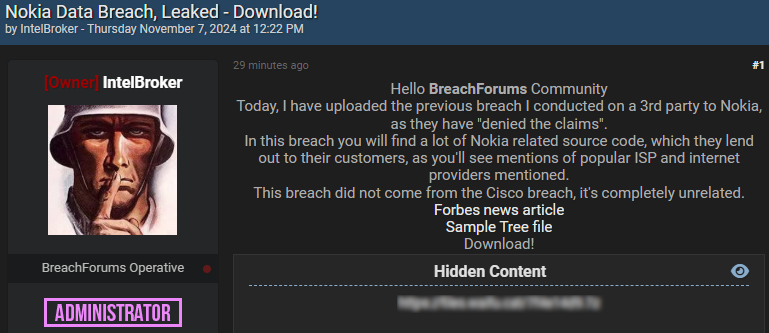
Source: BleepingComputer
In a statement to BleepingComputer, Nokia clarified that their ongoing investigation had unveiled the breach as being strictly tied to a third-party security incident, which impacted only a specific customized software application and not Nokia’s infrastructure as a whole.
“Our investigation has found no evidence of any of our systems or data being impacted. Our investigations point to a 3rd party security incident, related to a single customized software application,” – Nokia
Nokia emphasized that no critical systems or data—including their proprietary source code or encryption keys—are at risk from this breach, reassuring customers that their data and networks remain unaffected. The leaked source code pertains to an application not developed by Nokia but rather by a contractor, designed for exclusivity within a single network and devoid of any Nokia-specific code.
Despite the reassurance regarding their systems’ integrity, Nokia is continuing to monitor the situation diligently. The company is actively examining the implications of this third-party breach, which highlights the increasing vulnerabilities associated with third-party collaborations in today’s interconnected digital landscape.
