Last week, a series of domain hijacking incidents affected over a dozen organizations utilizing the services of the domain registrar Squarespace. This situation arose after Squarespace acquired the assets of Google Domains approximately a year ago, with many clients yet to establish their new accounts. Cybersecurity experts believe that malicious actors discovered a vulnerability allowing them to take control of any Squarespace accounts that were migrated but not yet configured by entering an email address associated with an existing domain.
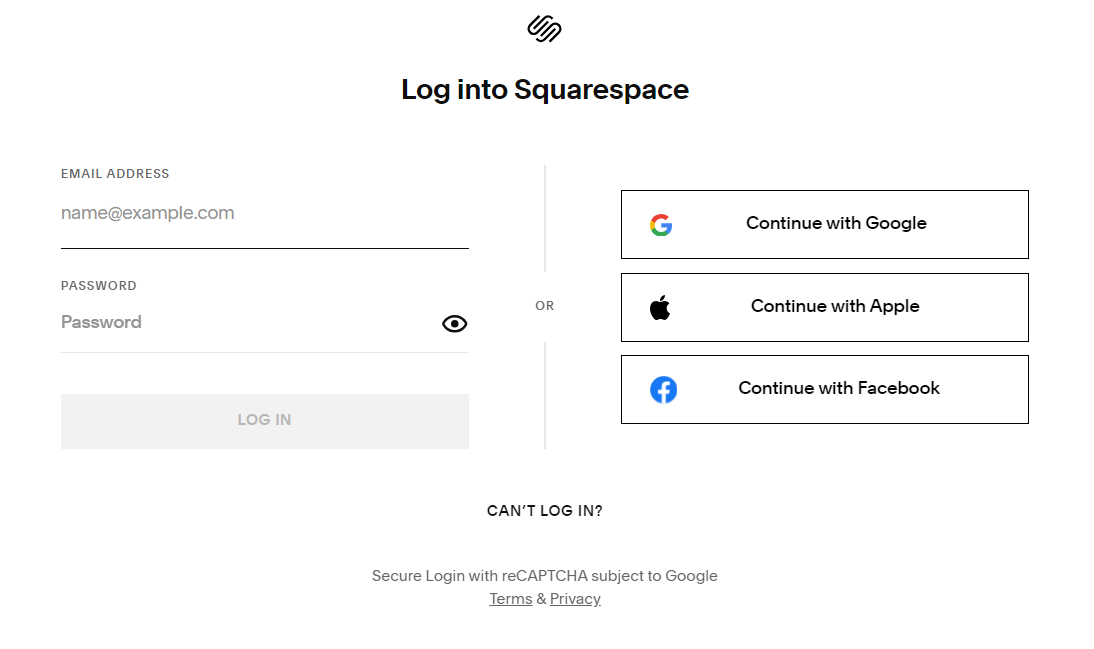
Previously, Squarespace’s website featured an option for logging in via email.
The hijackings, which transpired between July 9 and July 12, predominantly targeted cryptocurrency-related businesses, such as Celer Network, Compound Finance, Pendle Finance, and Unstoppable Domains. In some incidents, the attackers successfully redirected hijacked domains to phishing sites aimed at stealing cryptocurrency from unsuspecting visitors.
Headquartered in New York City, Squarespace integrated around 10 million domain names from Google Domains in June 2023 and has been in the process of transitioning those domains to its platform. However, the company has not publicly addressed the hijacking incidents or responded to requests for comment.
Research by cybersecurity experts from Metamask and Paradigm suggests that the most plausible reason behind these hijackings is Squarespace’s assumption that users migrating from Google Domains would predominantly opt for social login options, like “Continue with Google” or “Continue with Apple,” rather than choosing the less common “Continue with email” option. Taylor Monahan, Metamask’s lead product manager, indicated that Squarespace did not anticipate that a malicious actor might attempt to register an account using an email linked to a recently transferred domain before the legitimate email user could do so.
Monahan explained to KrebsOnSecurity, “As a result, nothing actually prevents them from trying to log in with an email. Without a password on the account, they are directed to the ‘create password’ flow, effectively giving them access to the domain since the account remains partially initialized on the backend.” Additionally, it was noted that Squarespace did not mandate email verification for accounts created using a password.
Monahan clarified that the domains moving from Google to Squarespace are identifiable, often through publicly available information about which email addresses hold admin rights for a domain. If the rightful email owner fails to set up their Squarespace account—perhaps due to various reasons like employee turnover—anyone who enters that email address into the Squarespace login form could gain full control over the domain.
Furthermore, researchers indicated that if attackers learned about email addresses linked to lower-privilege user accounts, such as “domain manager,” those accounts could also be vulnerable to hijacking and domain manipulation.

Squarespace indicates that domain owners and managers share similar privileges, including the capability to transfer a domain or manage DNS settings.
Monahan warned that the migration has reduced domain owners’ capacity to secure and monitor their accounts. “Squarespace lacks provisions for users who require some oversight of their account or domain activities. Users have limited control, no audit logs, and do not receive email notifications for many actions taken by a ‘domain manager,’ which presents significant security risks compared to Google’s previous offerings,” Monahan asserted.
The research team has released a detailed guide to enhance the security of Squarespace accounts, recommending users enable multi-factor authentication—previously disabled during the transition. “Recognizing which emails have access to your Squarespace account is a critical first step,” the guide emphasizes, noting many organizations may not be aware of existing accounts with such privileges.
This guidance also advises removing unnecessary Squarespace accounts and disabling reseller access within Google Workspace. “If you acquired Google Workspace through Google Domains, Squarespace is now your authorized reseller, meaning anyone with access to your Squarespace account may have a backdoor into your Google Workspace unless you explicitly restrict it based on the provided instructions,” the document cautions.
Update, July 23, 1:50 p.m. ET: In a recent post-mortem, Squarespace acknowledged the incidents, attributing the domain hijacks to “a weakness related to OAuth logins,” which the company claims to have addressed promptly. Their statement contradicts various findings of the mentioned research. “All compromised accounts relied on third-party OAuth. No changes to authentication protocols were made during the migration of Google Domains to Squarespace,” the post clarified, asserting that Squarespace accounts with unverified email logins were not compromised in the attacks.
