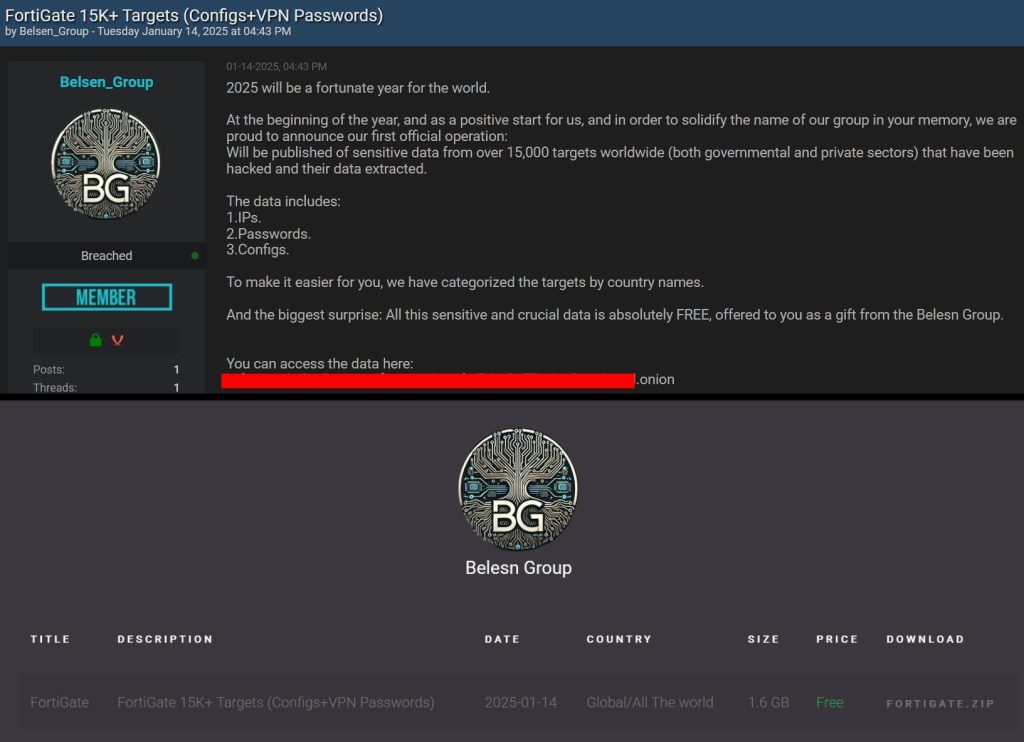
A significant leak involving over 15,000 configurations of FortiGate firewalls has been attributed to the hacker group known as Belsen Group. This breach poses a global risk to organizations utilizing these firewalls, which could lead to unauthorized access and compromise of sensitive systems. Strategies to mitigate this risk and strengthen cybersecurity defenses will be addressed.
The Belsen Group has unveiled a concerning breach, exposing the configurations of more than 15,000 FortiGate firewalls, impacting a wide array of organizations worldwide. This exposure places firms in multiple countries, including the United States, the United Kingdom, Poland, and Belgium, at heightened risk of compromise, as attackers can leverage the leaked configurations to bypass security measures and gain unauthorized access. Subsequent research indicates that France, Spain, Malaysia, the Netherlands, Thailand, and Saudi Arabia are also affected.
According to findings from CloudSEK’s XVigil digital risk platform, the Belsen Group exploited a zero-day vulnerability in 2022 to facilitate this leak. The exposed data encompasses crucial elements such as usernames, passwords (with some exposed in plain text), device management digital certificates, and comprehensive firewall rules. Collectively, this information provides malicious actors with extensive resources to exploit vulnerabilities within targeted organizations.
The exposure of usernames and passwords, particularly those in plain text, significantly increases risks, allowing attackers potential direct access to sensitive network systems. Organizations that patched the related vulnerability, identified as CVE-2022-40684, should nonetheless conduct thorough investigations for signs of compromise. Leaked firewall configurations can reveal internal network architectures, making it easier for adversaries to locate weaknesses and circumvent established security protocols.
Moreover, compromised digital certificates could enable unauthorized device access or impersonation during secure communications. This issue is exacerbated for organizations that implemented patches only after the initial breach; any access gained by attackers prior to the application of these updates continues to present a substantial threat.
Belsen Group’s Motives and History
Although the Belsen Group is relatively new to the hacker community, data from the breach suggests they have existed for at least three years. Analysts believe they exploited a zero-day vulnerability (CVE-2022-40684) in 2022, which facilitated access to a wide range of FortiGate firewalls. Following this exploitation, it appears they have transitioned to leaking data as of 2025, indicating a strategic evolution in their malicious activities.
Organizations are urged to take immediate action to address the potential risks stemming from this leak. Updating all device and VPN credentials, especially those listed in the exposed data, is critical. Implementing strong passwords, auditing firewall configurations, and fortifying access controls can significantly reduce vulnerabilities. Additionally, organizations should revoke and replace compromised digital certificates to maintain secure communications.
It is also advisable to document the timeline for addressing the CVE-2022-40684 vulnerability within your organization, conduct forensic assessments of affected devices, and actively monitor networks for any unusual activities. These proactive measures are essential for safeguarding your network and mitigating the risks associated with such breaches.
For those concerned about the implications of this latest breach, CloudSEK has made available a resource for organizations to verify if their network belongs to the exposed IPs in the leaked dataset, accessible here.