A significant cybersecurity incident surfaced today involving the brief compromise of at least 18 popular JavaScript code packages, which collectively receive over two billion downloads weekly. The breach occurred after a developer, engaged in maintaining these projects, fell victim to a phishing attack. While the immediate threat was contained—focused on cryptocurrency theft—experts caution that a more harmful variant could trigger widespread malware dissemination, challenging detection and mitigation efforts.
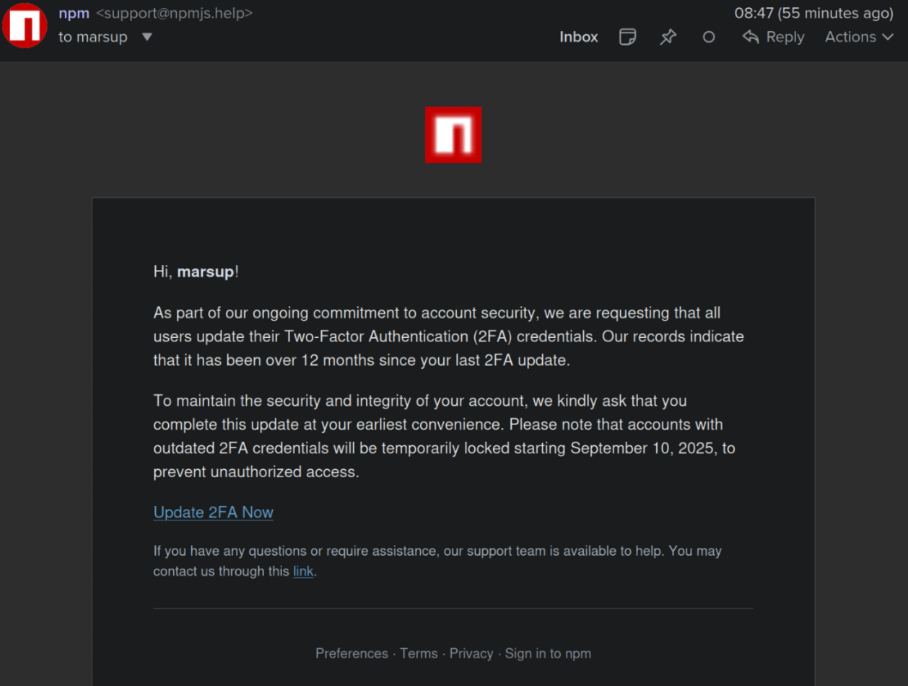
Phishing email tricked the developer into revealing NPM credentials, leading to the injection of malicious code in popular JavaScript packages.
Aikido, a cybersecurity firm based in Belgium, identified the malicious code within the affected libraries hosted on the Node Package Manager (NPM) platform. NPM serves as a central repository for JavaScript development, enabling developers to utilize pre-existing code instead of developing functions from scratch, particularly for common tasks like form submissions. While this practice enhances efficiency, it creates vulnerabilities that cybercriminals can exploit.
The attackers managed to introduce a code segment that covertly intercepts cryptocurrency transactions in user browsers. This code can manipulate wallet interactions, rerouting funds and approvals to accounts controlled by the attackers, while leaving no obvious signs for users. This type of threat reflects sophisticated tactics observed in the MITRE ATT&CK Matrix, particularly under initial access and execution guidelines, indicating that adversaries can gain entry through social engineering techniques.
Following the attack, Aikido utilized the social network Bsky to inform affected developer Josh Junon, who returned promptly with acknowledgment of the phishing incident that compromised his account. The phishing operation masqueraded as an urgent request for 2FA credential updates, using a fraudulent NPM login page to capture sensitive information. Once in control, attackers altered the account’s email address, effectively locking Junon out of his NPM profile.
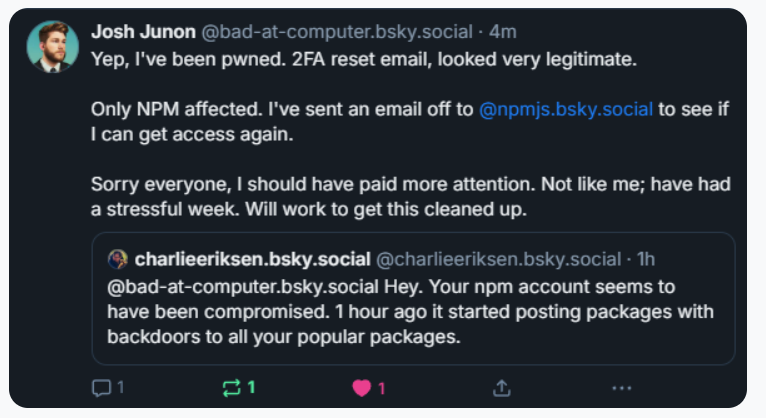
Aikido successfully notified the developer, who began addressing the compromised packages.
In a statement on HackerNews, Junon expressed remorse for the security lapse, emphasizing the high stakes involved. Philippe Caturegli, a security consultant, noted that the attackers had registered their deceptive domain mere days before executing the phishing scheme. This highlights the rapid adaptation of threat actors, who leverage tools and techniques to mount effective social engineering attacks, employing initial access and credential dumping methods as per the MITRE framework.
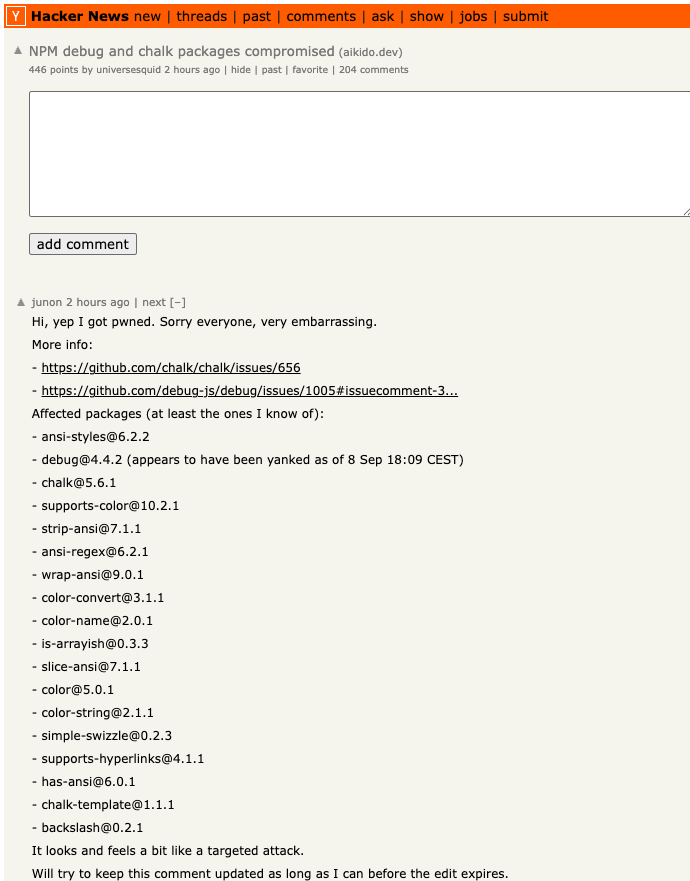
Junon’s acknowledgment of the incident was shared on HackerNews, detailing the packages affected.
Caturegli pointed out that the compromise had the potential for far more damaging consequences than those realized, as this incident reflects a broader vulnerability within the supply chain of software development. Aikido’s Eriksen concurred, highlighting the need for stricter verification methods for code submissions, emphasizing improved authentication processes that could help thwart these kinds of breaches.
Experts argue that the incident underscores the fragility of modern software ecosystems, where a small group of developers maintain code that global infrastructures depend upon. Consequently, ongoing reliance on easily phishable two-factor authentication systems poses a significant risk. Nicholas Weaver, a researcher with the International Computer Science Institute, called for comprehensive adoption of phish-proof authentication mechanisms, advocating for the use of physical security keys that remain impervious to phishing attempts.
As the landscape of cybersecurity continues to evolve, incidents like these serve as critical reminders of the inherent vulnerabilities within widely-used code libraries and the supply chain model at large. For organizations leveraging these resources, bolstering security protocols should remain a top priority to mitigate the risks posed by such supply chain threats.
