Cybersecurity firm Resecurity has issued a robust defense against allegations made by the hacking group ShinyHunters, who claimed earlier today to have infiltrated the company’s internal systems and extracted sensitive data. Resecurity stated that the interaction reported by the attackers was with a honeypot, not with its authentic infrastructure.
ShinyHunters’ Allegations
On January 3, ShinyHunters announced via their Telegram channel that they had acquired “full access” to Resecurity’s internal systems. The group purported that they had accessed a variety of sensitive information, including employee records, internal communications, threat intelligence documents, and customer data. They also circulated multiple screenshots that they claimed demonstrated access to backend dashboards, user profiles, authentication tokens, and internal discussions. This leak was framed as a retaliatory action, with ShinyHunters alleging that Resecurity had previously attempted to engage with them through deceptive tactics, posing as fictitious buyers on dark web forums.
Resecurity’s Defense
In response, Resecurity provided a comprehensive statement to Hackread.com, referencing a December 2025 blog post titled “Synthetic Data: A New Frontier for Cyber Deception and Honeypots.” The company asserted that the hackers had interacted with a simulated environment designed to attract and log unauthorized activity. This honeypot environment included synthetic employee accounts, fake applications, and isolated infrastructure that had no connection to actual operations or clients.
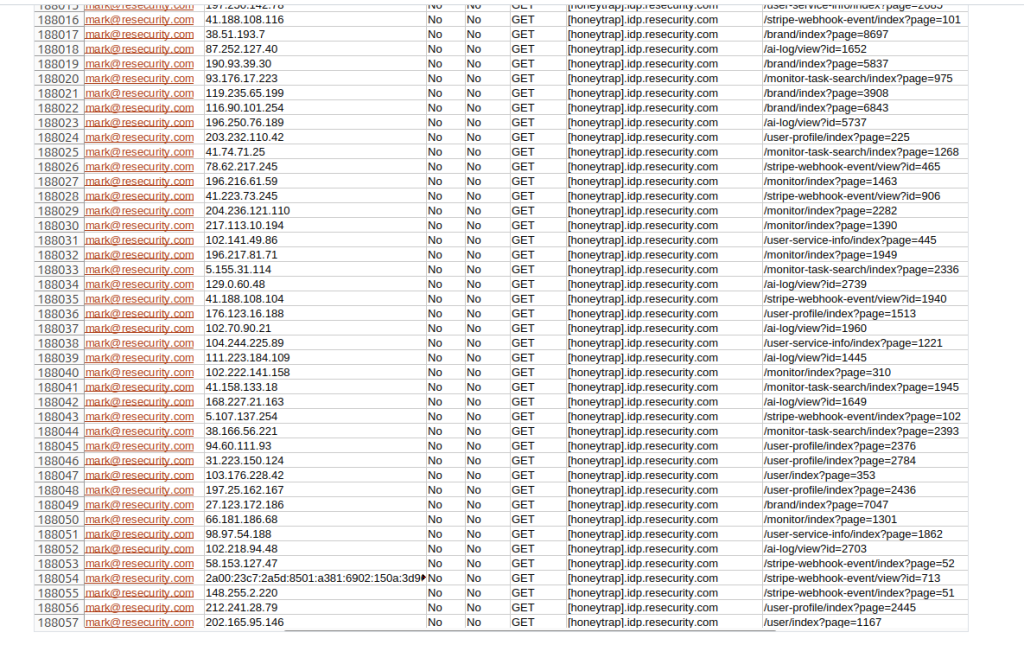
Further bolstering their position, Resecurity revealed details of how a decoy was introduced into the dark web environment through a bait account. Evidence supporting their claims was shared with Hackread.com, including logs of the attackers’ interactions and screenshots showing access to non-existent accounts such as [email protected].
A screenshot published by Resecurity depicted the attackers’ activity mapped across various IP addresses, some of which were identified as real due to proxy failures. Resecurity argues that this evidence confirms the honeypot was effective, capturing detailed behavior data regarding the attackers’ actions.
No Actual Impact Reported
Resecurity emphasized that no real client data, operational systems, or passwords were compromised during this incident. The honeypot was isolated from the company’s production environments, resulting in no disruption or breach of actual assets. Additionally, they highlighted that the use of synthetic data and deception tactics is a well-established counterintelligence strategy aimed at understanding and studying potential threat actors.
To provide further context, Resecurity referenced a previous blog post from September 2025 that detailed activities involving groups like ShinyHunters, suggesting that this incident might be partly motivated by their ongoing exposure of such cybercriminal organizations.
Conclusion
While ShinyHunters characterized their actions as a significant breach, Resecurity’s denial, supported by evidence that aligns with the characteristics of a honeypot strategy, indicates that the episode may have served to mislead the attackers and document their behavior. As the situation unfolds, further insights may emerge regarding the authenticity of these claims, but current indications suggest the honeypot effectively mitigated the perceived threat.