Fraud Management & Cybercrime,
Social Engineering
Malware Dissemination Tied to FileFix Campaign Targeting Facebook Users
A new social engineering operation, dubbed FileFix, has emerged, employing sophisticated techniques to persuade users into downloading malware, disguising the act as an effort to address wrongful suspensions of their Facebook accounts.
This technique is a variant of the ClickFix attack, a method that has gained traction over the past year, whereby users are manipulated into executing malicious code under the pretense of fixing a technical issue. A hacker known as “mr. d0x” revealed an alternative approach in June, shifting the manipulation focus to the widely recognized Windows File Explorer interface.
According to researchers from backup and recovery firm Acronis, this newly identified FileFix campaign represents a “rare in-the-wild example” of advanced social engineering tactics. The perpetrators have invested considerable effort into crafting a more sophisticated approach than the traditional ClickFix methods.
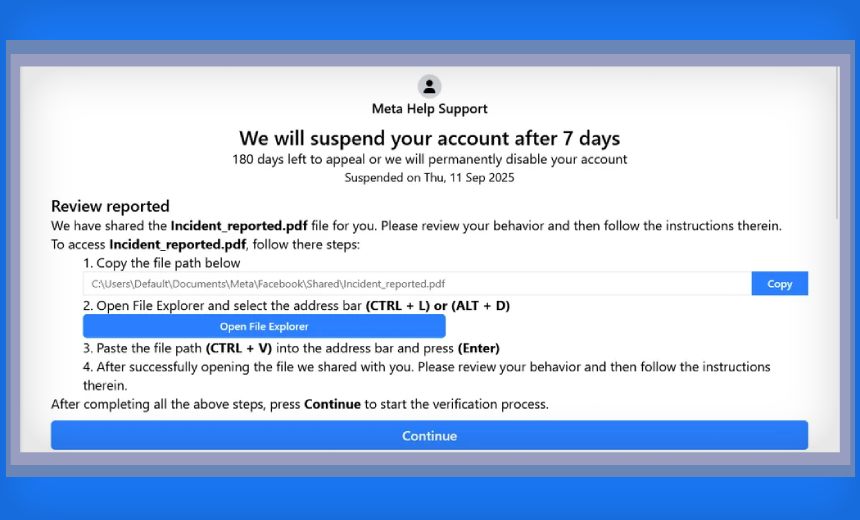
Victims are typically ensnared through phishing emails containing a link that directs them to a fraudulent message purportedly from “Meta Help Support.” This message warns users of an impending suspension of their Facebook accounts, unless they take steps to file an appeal.
The linked site instructs the user to open File Explorer to access a purported PDF shared by Facebook. However, the “File Explorer” they attempt to open is actually a file upload interface, into which they are led to paste a malicious command disguised within an innocuous file path.
Upon proceeding, victims receive a notification stating that “No file is found,” and are prompted to “Please complete the steps.” While this occurs, a harmful PowerShell script is executing in the background. Notably, the script’s initial action involves downloading an image that encodes a hidden payload, which is subsequently parsed to extract and execute malicious code.
This initial stage decrypts and decompresses various payloads, which may include DLL and executable files, often run through conhost.exe before erasing their traces. The campaign launches a loader developed in Go, which conducts sandbox checks to evade detection, encrypts strings to hinder analysis, and ultimately delivers StealC, an info-stealer adept at harvesting credentials from browsers, cryptocurrency wallets, messaging applications, and cloud-based services.
StealC ranks among the most prominent info-stealers featured in dark web forums, alongside others such as Lumma and RedLine. This variant exhibits rapid evolution, showcasing improved command-and-control capabilities and advanced data-exfiltration features.
The campaign has translated its phishing mechanisms into multiple languages, demonstrating a flexible approach. Indicators of compromise suggest that this activity has a global reach, with connections to the United States, Germany, China, among other nations, indicating an opportunistic rather than a targeted approach toward victims.