Encryption & Key Management,
Security Operations
Researcher Unveils Bitpixie Attack Techniques to Extract Encryption Keys
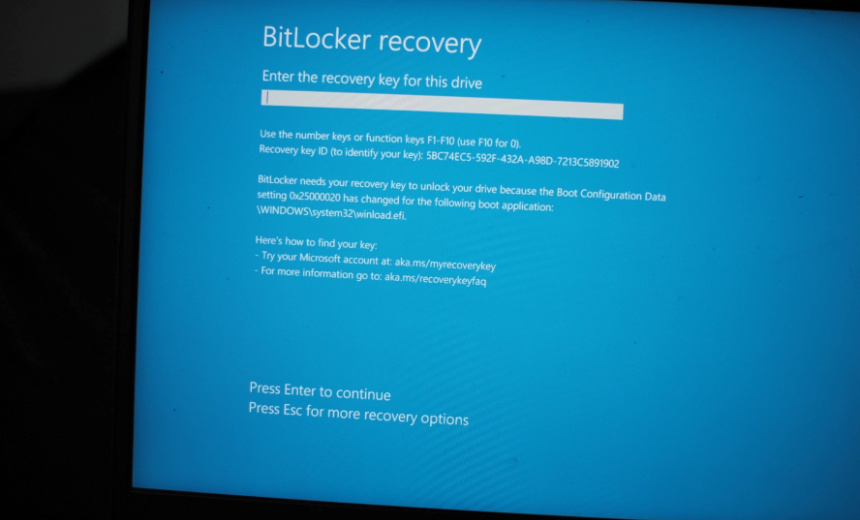
Recent research has unveiled a previously addressed vulnerability within the Windows BitLocker disk encryption system that remains exploitable. This flaw poses significant risks, potentially allowing attackers to decrypt sensitive information and compromise data integrity.
During a presentation at the recent Chaos Communication Congress in Germany, security researcher Thomas Lambertz highlighted that a Microsoft patch aimed at mitigating the medium severity vulnerability, identified as CVE-2023-21563, does not effectively eliminate the threat. Contrary to Microsoft’s assessment, Lambertz asserted that this flaw is susceptible to network-based exploitation.
Lambertz detailed the mechanics of the “bitpixie” attack, which leverages inherent weaknesses in the way Windows handles memory and encryption during boot processes. By rebooting a fully updated Windows 11 device in recovery mode and using an older bootloader, he successfully orchestrated an environment that bypassed encryption protection.
The key to this exploit lies in the ability of the researcher to manipulate the recovery process, ultimately making the device “forget” its encryption key. Lambertz emphasized that he gained access to critical system memory, extracting vital information, including the master key necessary for decryption. This method marks a sophisticated use of network techniques, with Lambertz noting that the only effective countermeasure is to disable the entire network stack within the BIOS settings, thereby prohibiting PXE booting attacks.
Despite Microsoft’s ongoing efforts to remediate this issue, Lambertz indicated that the company faces challenges in balancing effective patching with the risk of disrupting legacy devices during firmware updates. Consequently, Microsoft has been cautious, as they recognize that unintended consequences could lead to further vulnerabilities within BitLocker.
In a potential shift for the future, Lambertz mentioned that Microsoft might not renew its current boot certification regulations post-2026. However, this move could introduce greater risks by allowing the use of outdated and insecure certificates, raising concerns about the overall security landscape. At the time of this report, Microsoft had not provided comment on the ongoing situation.
In the context of the MITRE ATT&CK framework, this incident illustrates tactics such as initial access through exploitation and potential privilege escalation as attackers gain unauthorized access to critical systems. The vulnerabilities associated with BitLocker underscore the importance of staying vigilant and proactive in cybersecurity measures, particularly as threats evolve within the digital landscape.