A ransomware group known as Dark Angels has garnered attention following reports of a record-breaking $75 million ransom payment by a Fortune 50 company. Security analysts confirm that Dark Angels has been active since 2021, although they often evade media scrutiny by operating independently and maintaining a low profile, targeting one victim at a time. Their strategy prioritizes mass data theft over disruptive tactics that typically cripple a victim’s operations.

Image: Shutterstock.
According to Zscaler ThreatLabz, Dark Angels has been identified as the most significant ransomware threat for 2024, particularly highlighted by the substantial ransom payment reported in early 2024. This amount surpasses all previous ransom records attributed to ransomware attacks. ThreatLabz observed that Dark Angels executed some of the largest ransomware incidents thus far, yet their operational details remain largely obscure.
Brett Stone-Gross, the senior director of threat intelligence at ThreatLabz, noted that Dark Angels employs a distinct operational model compared to other ransomware factions. Unlike the prevalent affiliate model, which often relies on a network of hired hackers to deploy malicious software, Dark Angels operates independently.
Stone-Gross remarked, “They have no desire to seek media attention or create operational chaos.” Their primary goal appears to be profit, achieved with minimal visibility. Unlike typical ransomware groups that prominently feature victim leak sites as a means of extortion, Dark Angels only established such a site, known as Dunghill Leak, in April 2023, following their usual low-key approach.
The Dark Angels victim shaming site, Dunghill Leak.
“Their operations are not characterized by ostentation,” Stone-Gross added. “For a long while, they avoided creating a headline-worthy presence but might have felt pressured to launch their leaks site to demonstrate their commitment to releasing stolen information.” Dark Angels is believed to be a cybercrime syndicate based in Russia, specializing in the large-scale theft of sensitive data from multiple sectors, including healthcare, finance, government, and education. In instances involving large organizations, they have been known to extract anywhere from 10 to 100 terabytes of data, a process that can take several days or weeks.
As with many ransomware groups, Dark Angels threaten to publish stolen data if their ransom demands are ignored. Notable victims listed on Dunghill Leak comprise the global food distribution company Sysco, which reported a ransomware attack in May 2023, and Sabre, a major travel booking platform, which fell victim to a Dark Angels attack in September 2023.
Stone-Gross highlighted that Dark Angels tends to avoid deploying ransomware malware in a manner that severely disrupts IT operations, as such incidents typically lead to widespread media coverage. “They strategically determine whether to utilize ransomware based on the potential for disruption. Their focus remains on data acquisition rather than simply locking systems to extort victims for ransom,” he noted.
Regarding the recent $75 million ransom, speculation points to Cencora (formerly known as AmeriSourceBergen Corporation) as the victim. The firm disclosed to the U.S. Securities and Exchange Commission (SEC) about a data security incident on February 21, 2024, prompting industry discussions about potential ties to the Dark Angels payment. Cencora, ranked #10 on the Fortune 500 list with over $262 billion in revenue last year, has not confirmed whether it paid a ransom but provided financial details that suggest significant costs associated with the breach.
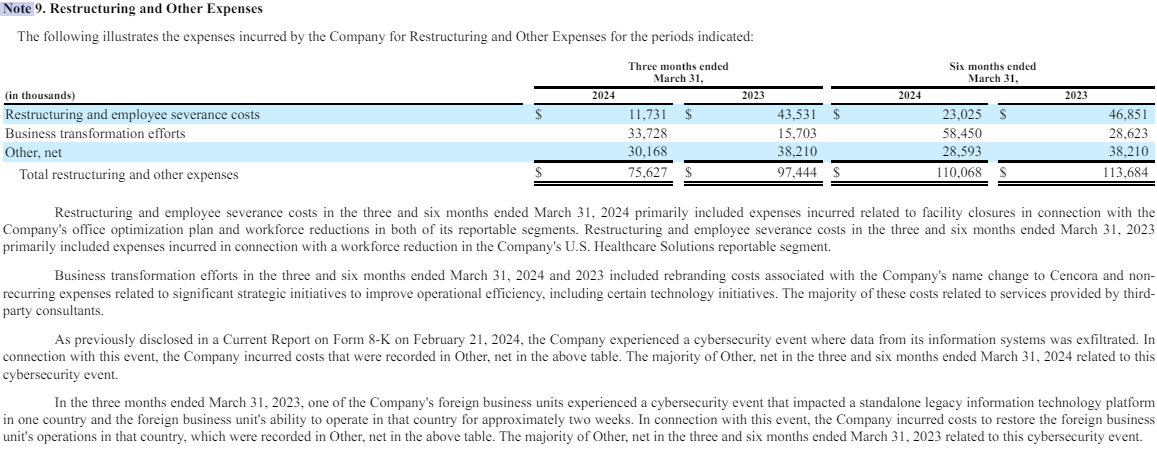
Cencora’s 2024 1st quarter report documents a $30 million cost associated with a data exfiltration event in mid-February 2024.
In the most recent State of Ransomware report conducted by Sophos, findings indicate that the average ransom payment has surged fivefold within a year, rising from $400,000 in 2023 to $2 million in 2024. The report also highlights that over 80% of ransom funding sources are diversified, with 40% derived directly from the affected organizations and 23% from insurance companies.
This recent incident involving Dark Angels underscores the evolving sophistication of ransomware operations, which warrant close attention from businesses across sectors, especially those in the U.S. As cyber threats continue to escalate, understanding the tactics employed by such groups, as outlined in the MITRE ATT&CK framework—including initial access, data exfiltration, and impact—becomes increasingly critical for organizations aiming to protect their data and infrastructure.